This article is presenting how to use the Hacker Typer at Pranx.com. This Geek Typer is meant to simulate that you’re hacking a top secret government facility. Use the program in full screen mode (Ctrl+F5) to hide the browser frame and make it even more life-like. Use the program to prank someone, making them believe that you’re a real hacker.
However the site works well on mobile devices, you will have the best user experience on a desktop computer or on any other wide screen device.
The Geek Typer starts with an empty Windows-like desktop interface with icons on the right, a taskbar and an open Start menu with useful How to use information. Click anywhere outside the Start menu to minimize the welcome text and make the website go full screen. You can manually toggle full screen mode with the F11 key in Windows and Ctrl+Cmd+F on a Mac.

The welcome message gives you the possibility to automate the hacking. Press the red Automate button to open some programs and animate the typing. You can sit back and relax because it runs automatically until you stop it by pressing a button on your keyboard. You can still open, close and move the windows around.
A cursor line is supposed to blink in the top left corner of the screen when you close the welcome screen. This means that you can start pressing random buttons on your keyboard and the hacker code will be automatically added to the screen, four characters at a time to make your fingers look faster.
Hacker Programs
Open various programs with the icons on the right of the screen. These work like regular operating system windows. You can minimize them to the taskbar, make them go full screen or close them. Most of them are resizable by dragging the bottom-right corner of the open window.
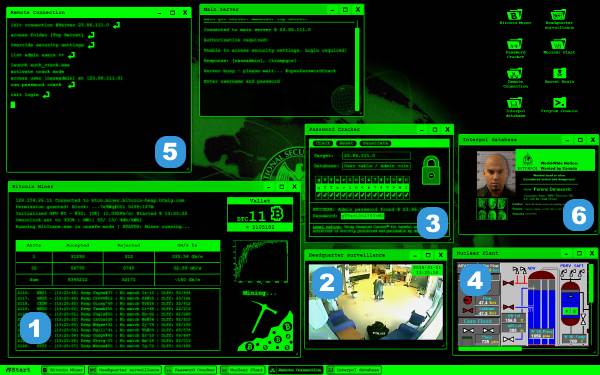
Bitcoin Miner
Cryptocurrencies are extremely popular these days, especially Bitcoin which is worth thousands of dollars. People use advanced softwares to “mine” it. The online Bitcoin miner simulator will create the illusion that you’re in the process of mining valuable Bitcoins. You start with 8 BTC and your wallet will keep growing as you run the program. Show this screen to your friends and they’ll think that you’ve become really wealthy.
This program has a start button and it runs automatically. You can’t interact with the program once it has been started.
Headquarter surveillance
A webcam shows as a bank is being robbed by gunmen. This is just a looping video which you can pause clicking the screen.
Password cracker
Simulate a brute-force attack on a server. The cracker will try to guess a password through an animated sequence. Start the process with the Crack button and stop it with the Reset.
Nuclear power plant controller
The power plant control room screen is showing randomly changing values and levels. You can’t interact with this screen.
Remote server connection
Connect to a server through a console interface and hack it entering commands. This program opens two windows: the console and the remote server.
All you have to do is type on your keyboard randomly when the console input cursor is blinking. This will enter commands and the server will respond accordingly. Some commands will trigger windows like the “Access denied” alert or the “Password Cracker”.
Alerts
Open alert windows on the screen with the number buttons on your keyboard. These windows are all passive, you can’t interact with them:

They open in the center of the screen but you can move them around dragging them with your mouse, and close them with the little X on their top corners. Close all open alert boxes with the Space button. You can close them with the Esc button too, but that exits the full screen view.
The open alert boxes don’t show in the taskbar.
List of passive alerts:
- Satellite geolocation tracking on a map
- Access denied warning
- Permission granted
- Installing malware progress bar
- Self destruct countdown
- Neural network tracing animation
- Matrix digital rain
- Graph animation
- Downloading confidential data
- Top secret warning
This website was created using the Windows template from HTML5-templates.com using HTM, CSS and JavaScript.
Special thanks to HTML Fiddle for making our life easier!